Your entire network, protected globally in hours, not months.
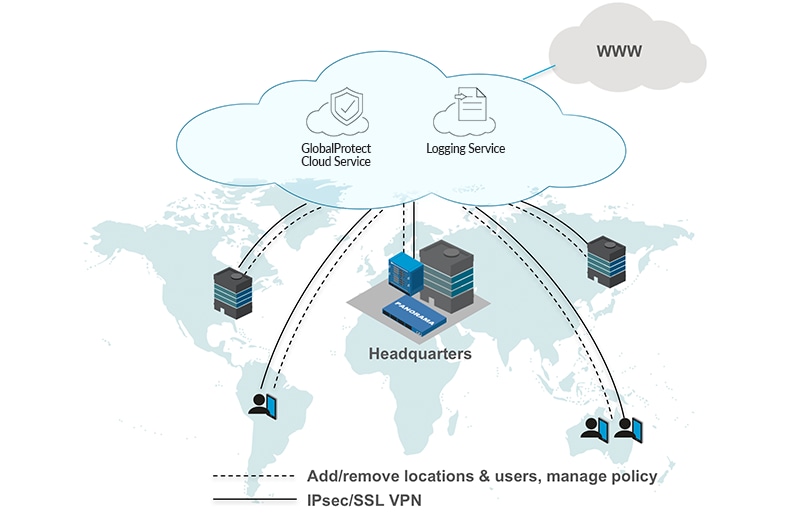 As the workforce and commonly used applications become more widely distributed, the operational challenges associated with protecting remote networks and mobile users often result in security policy inconsistencies. Organizations continually look for an alternative approach to secure remote networks and users that enables strong, consistent security with a lowered operational effort.
As the workforce and commonly used applications become more widely distributed, the operational challenges associated with protecting remote networks and mobile users often result in security policy inconsistencies. Organizations continually look for an alternative approach to secure remote networks and users that enables strong, consistent security with a lowered operational effort.GlobalProtect cloud service reduces the operational burden associated with securing your remote networks and mobile users by leveraging a cloud-based security infrastructure managed by Palo Alto Networks. Based on our next generation security platform, administrators can manage GlobalProtect cloud service with Panorama to create and deploy consistent security policies for all remote networks and mobile users. The GlobalProtect cloud service shared ownership model allows you to move your remote networks and mobile user security expenditures to a more efficient and predictable OPEX-based model.
Download “Palo Alto GlobalProtect Cloud Service Data Sheet.pdf” Palo-Alto-GlobalProtect-Cloud-Service-Data-Sheet.pdf – Downloaded 1775 times – 1.09 MB





 To help identify connecting endpoints, legacy practices often meant deploying comprehensive endpoint management solutions, agents, and manually updating multiple endpoint databases. None of these delivered the desired results because IT was overwhelmed by BYOD, guest access deployments, and rogue wired and wireless endpoints; many of which come and go with users.
To help identify connecting endpoints, legacy practices often meant deploying comprehensive endpoint management solutions, agents, and manually updating multiple endpoint databases. None of these delivered the desired results because IT was overwhelmed by BYOD, guest access deployments, and rogue wired and wireless endpoints; many of which come and go with users. Gartner is forecasting 50 billion connected devices by 2020. Laptops, smartphones, tablets and Internet of Things (IoT) devices are pouring into the workplace. With every employee now utilizing an average of three devices, the addition of IoT increases the vulnerabilities inside the business – adding to the operational burden.
Gartner is forecasting 50 billion connected devices by 2020. Laptops, smartphones, tablets and Internet of Things (IoT) devices are pouring into the workplace. With every employee now utilizing an average of three devices, the addition of IoT increases the vulnerabilities inside the business – adding to the operational burden. The VM-Series is a virtualized form factor of our next-generation firewall that can be deployed in a range of private and public cloud computing environments based on technologies from VMware®, Amazon® Web Services, Microsoft®, Citrix® and KVM.
The VM-Series is a virtualized form factor of our next-generation firewall that can be deployed in a range of private and public cloud computing environments based on technologies from VMware®, Amazon® Web Services, Microsoft®, Citrix® and KVM. Palo Alto Networks is the next-generation security company maintaining trust in the digital age by helping tens of thousands of organizations worldwide prevent cyber breaches. With our deep cybersecurity expertise, commitment to innovation, and game-changing Next-Generation Security Platform, customers can confidently pursue a digital-first strategy and embark on new technology initiatives, such as cloud and mobility. This kind of thinking and know-how helps customer organizations grow their business and empower employees all while maintaining complete visibility and the control needed to protect their critical control systems and most valued data assets.
Palo Alto Networks is the next-generation security company maintaining trust in the digital age by helping tens of thousands of organizations worldwide prevent cyber breaches. With our deep cybersecurity expertise, commitment to innovation, and game-changing Next-Generation Security Platform, customers can confidently pursue a digital-first strategy and embark on new technology initiatives, such as cloud and mobility. This kind of thinking and know-how helps customer organizations grow their business and empower employees all while maintaining complete visibility and the control needed to protect their critical control systems and most valued data assets.